Key Takeaways
- Data breaches cost $4.44M globally, $10.22M in U.S., Home Depot paid $179M for centralized database vulnerability
- Traditional payments store credentials in centralized databases, creates “honeypot” architecture attackers repeatedly exploit
- Home Depot was PCI compliant when breached, compliance secures the honeypot but doesn’t eliminate it
- Blockchain payments store zero credentials, no database to breach, private keys never transmitted
- 50%+ lower transaction costs (1% vs. 3%) enable customer discounts while maintaining margins
- Hybrid model recommended: Add blockchain alongside cards, shift volume incrementally, reduce PCI scope over time
- Torsion provides 2-4 week e-commerce integration with Shopify, WooCommerce, Magento, no blockchain expertise required
September 8, 2014. Home Depot’s security team detected unusual network activity. By the time they contained the breach, attackers had exfiltrated 56 million credit and debit card numbers. In November, the damage assessment grew worse: another 53 million customer email addresses stolen.
The attack vector: A third-party HVAC vendor named Fazio Mechanical. Attackers phished the vendor’s credentials, pivoted into Home Depot’s corporate network through vendor access, exploited a Windows zero-day vulnerability, and installed “BlackPOS” memory-scraping malware on 7,500 self-checkout terminals.
Total cost: $179 million in legal fees, regulatory violations, customer reparations, and security remediation.
The eerie part? This was the exact same attack that hit Target 10 months earlier, 70 million customers compromised through an HVAC vendor phishing attack. Same vulnerability. Same methodology. Same catastrophic outcome.
Fast forward to October 2025. The average data breach now costs $4.44 million globally and $10.22 million in the United States, an all-time high for any region. E-commerce fraud losses: $48 billion annually. Every $100 in fraudulent orders results in $207 in total business losses. And 53% of all data breaches still target customer PII, with payment card data the most valuable target.
The question CISOs keep not asking: Why are we still building payment systems with the same architectural vulnerability that cost Home Depot $179 million?
The answer isn’t better database encryption, stronger access controls, or more expensive PCI DSS compliance. The answer is eliminating the database entirely.
Blockchain payment rails don’t make the honeypot more secure. They remove the honeypot.
The “Honeypot” Architecture: Why Traditional Payments Are Built to Be Breached
Before understanding why blockchain payments eliminate breach vulnerabilities, we need to understand why traditional payment systems create them.
How Centralized Payment Databases Become Irresistible Targets
Every e-commerce company using traditional payment processing follows the same architecture:
- Customer enters credit card details at checkout (card number, CVV, expiration date, billing address)
- Merchant stores these credentials in a centralized database
- When future transactions occur, merchant validates against this stored data
- Result: A single database contains millions of payment credentials
Why this architecture exists: Card networks (Visa, Mastercard, American Express) designed the system this way. Merchants need to validate transactions against stored credentials to process payments through the card network infrastructure.
The honeypot effect: In cybersecurity, a “honeypot” is an intentionally vulnerable system designed to attract attackers for research purposes. Centralized payment databases function as unintentional honeypots, they concentrate millions of high-value credentials in a single location that becomes an irresistible target.
The mathematical problem: One successful breach compromises millions of records. Home Depot: 56 million cards. Target: 70 million customers. The attack surface isn’t distributed, it’s concentrated.
Inside the Home Depot Breach: The Technical Mechanics
The Home Depot incident provides a textbook example of how centralized payment databases get compromised:
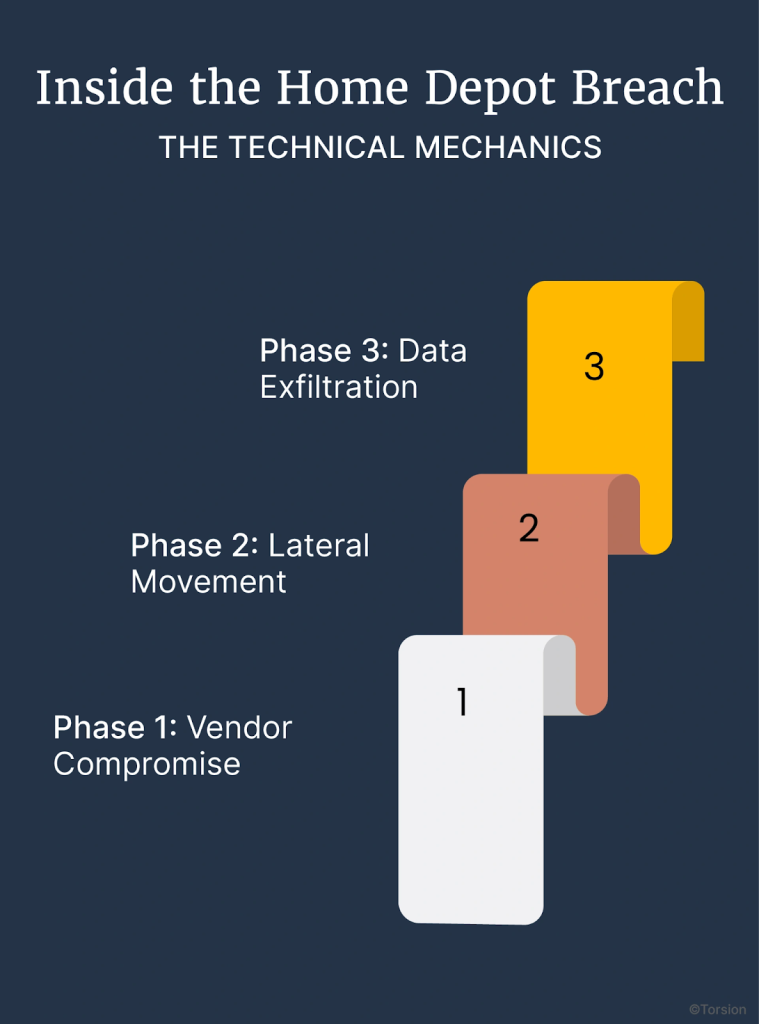
Phase 1: Vendor Compromise
- Attackers targeted Fazio Mechanical, a third-party HVAC contractor with network access to Home Depot systems
- Phishing emails stole vendor credentials
- Vendor had legitimate access to Home Depot’s network for maintenance purposes
Phase 2: Lateral Movement
- Using Fazio’s credentials, attackers pivoted from vendor environment into Home Depot’s corporate network
- Exploited a Windows zero-day vulnerability to gain elevated privileges
- Moved laterally until they located the payment processing environment
Phase 3: Data Exfiltration
- Installed custom “BlackPOS” malware on 7,500 self-checkout terminals
- Malware scraped payment card data from memory as transactions processed
- Exfiltrated 56 million credit/debit cards + 53 million email addresses from centralized database
The critical point: Home Depot was PCI DSS compliant when this breach occurred. They had firewalls, encryption, access controls, vulnerability scanning, all the required security controls. The problem wasn’t compliance failure. The problem was architectural.
PCI DSS compliance makes the honeypot harder to access. But the honeypot still exists. Attackers who bypass perimeter controls find millions of credentials concentrated in one database.
The Pattern That Keeps Repeating
Home Depot wasn’t an isolated incident. It was the second time in 10 months that an identical attack vector compromised a major retailer:
- December 2013: Target breach (70M customers, third-party HVAC vendor phishing attack)
- September 2014: Home Depot breach (56M cards, identical methodology)
- 2014-2015: Multiple additional retailers using the same architecture suffered similar breaches
The commonality: Centralized databases storing payment credentials created single points of catastrophic failure. Third-party vendor access provided the entry point, but the centralized database was the ultimate target.
The PCI Compliance Paradox: Spending Millions to Secure the Vulnerability
After Target and Home Depot, the industry response was predictable: More PCI DSS compliance spending.
What PCI DSS Actually Requires (And Costs)
PCI DSS (Payment Card Industry Data Security Standard) mandates comprehensive security controls for any entity storing, processing, or transmitting payment card data:

The Cost Reality
| Merchant Level | Annual Transactions | Implementation Cost | Annual Maintenance |
| Level 1 | >6 million | $550K – $1M | $250K |
| Level 2 | 1-6 million | $260K – $500K | $100K |
| Level 3 | 20K – 1M | $75K – $200K | $50K |
| Level 4 | <20K | $30K – $90K | $35K |
Additional ongoing costs:
- Quarterly vulnerability scans: $2,400 – $24,000 annually
- Qualified Security Assessor (QSA) audit fees: $15,000 – $75,000
- Remediation costs when gaps found: $5,000 – $100,000+ per finding
- Security tools and technology: $10,000 – $50,000+ annually
What PCI Compliance Doesn’t Eliminate
Here’s the uncomfortable truth: PCI DSS doesn’t eliminate the architectural vulnerability.
You still must:
- Store payment credentials (even if tokenized/encrypted)
- Maintain a centralized database as attack target
- Grant third-party vendor access for legitimate business purposes
- Accept that humans can be phished, credentials can be stolen, and perimeter controls can be bypassed
The Home Depot lesson: They were PCI compliant. They had the required controls. They still lost $179 million.
The fundamental issue: PCI DSS secures the honeypot. It doesn’t eliminate it.
For a Level 1 merchant, that’s $1 million implementation + $250,000 annual maintenance to secure an architecture that’s fundamentally vulnerable to the same attack pattern that’s worked since 2013.
How Blockchain Payment Rails Eliminate the Vulnerability
Blockchain payments don’t improve database security. They eliminate the need for a database of credentials entirely.
The Architectural Difference That Matters
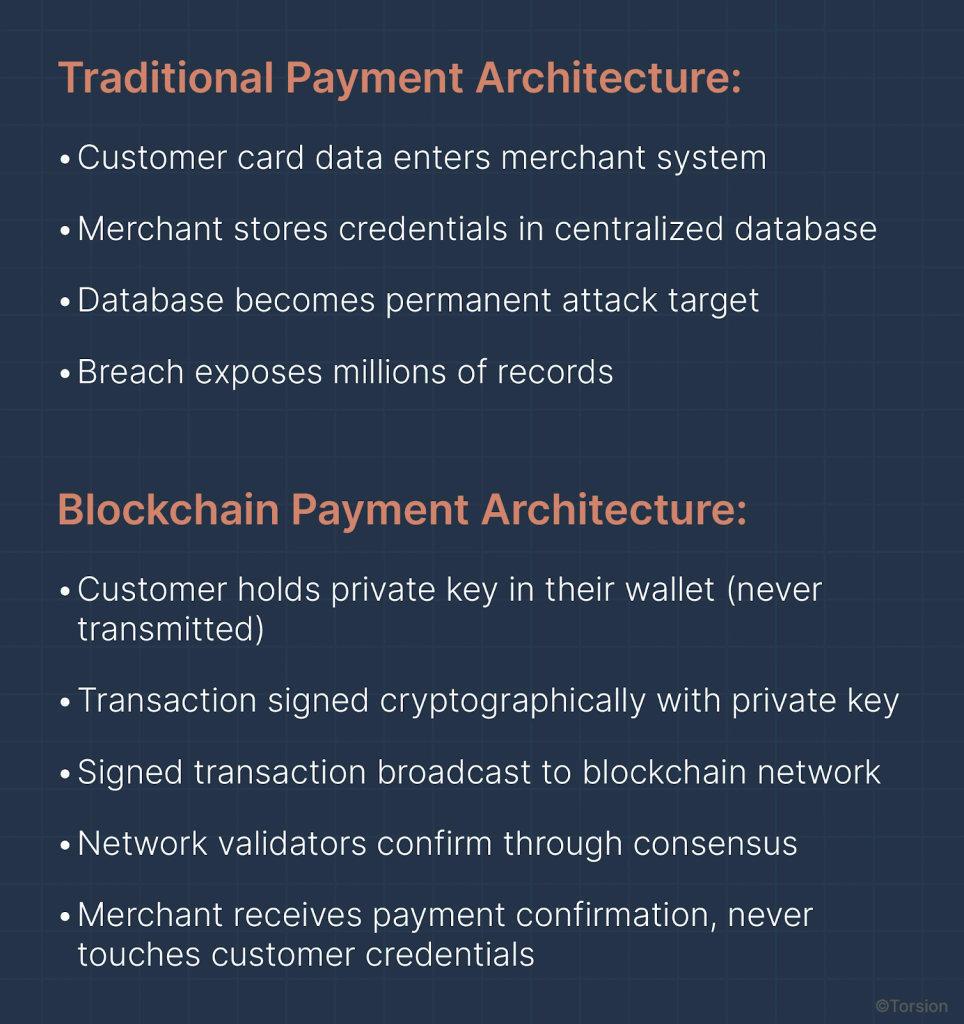
The security paradigm: Traditional payments centralize credentials. Blockchain payments decentralize validation. The merchant never stores payment data, because validation happens on the network, not in their database.
How Blockchain Transactions Actually Work (Without the Jargon)
Let’s walk through a blockchain payment at checkout:
Customer Side:
- Selects “Pay with USDC” (stablecoin maintaining $1 peg)
- Wallet interface displays payment amount and merchant’s blockchain address
- Customer clicks “Authorize” (doesn’t enter card number, CVV, or any credentials)
- Wallet uses customer’s private key (stored locally on their device) to create cryptographic signature
- Transaction broadcasts to blockchain network
Merchant Side:
- Receives notification: “Payment pending, awaiting network confirmation”
- Network validators confirm transaction through consensus (typically minutes)
- Payment confirmed, order fulfillment begins
- Merchant’s database never stored customer payment credentials
What Gets “Stored” on Blockchain:
- Public addresses (like account numbers, but not sensitive, analogous to email addresses)
- Transaction hashes (unique IDs proving payment occurred)
- NOT stored: Private keys, personal information, payment credentials
Blockchain payments are like using a unique, single-use credit card number for every transaction, except the merchant never sees any card number at all. They just receive mathematical proof that payment happened.
The Four Security Principles That Change Everything

1. Decentralization: No Central Database to Target
Traditional payments: Attack one database, compromise millions of records.
Blockchain payments: Network distributed across thousands of nodes worldwide, no single database holding credentials.
Attack difficulty: To compromise blockchain payments, attacker must control 51% of network computational power. For Bitcoin: estimated $20 billion cost. For Ethereum: even higher. Compare that to phishing a vendor’s credentials (Home Depot’s $179M breach cost).
2. Cryptographic Security: Private Keys Never Transmitted
Traditional payments: Customer enters card number, CVV, expiration, transmitted to merchant, stored in database.
Blockchain payments: Private key stays on customer’s device, creates digital signature proving ownership. Signature proves transaction authorization without revealing the key itself.
Phishing immunity: Even if attacker intercepts transaction data, they get public addresses and transaction hashes, useless without the private key that never left customer’s wallet.
3. Immutability: Permanent, Unalterable Audit Trail
Traditional payments: Database records can be altered by attackers with sufficient access.
Blockchain payments: Each transaction cryptographically linked to previous transactions in “blocks.” Altering one transaction requires rewriting entire blockchain history, computationally infeasible.
Audit benefit: Every payment permanently verifiable on blockchain. Can’t be tampered with retroactively. Built-in fraud detection.
4. Consensus Validation: Network Agrees on Transaction Validity
Traditional payments: Merchant’s database validates against card network.
Blockchain payments: Distributed network of validators independently confirm transaction legitimacy.
No central point of failure: Merchant doesn’t need to maintain validation infrastructure. Network handles it. Merchant receives confirmation that payment cleared.
Security Comparison: Honeypot vs. Cryptographic Validation
| Attack Vector | Traditional Payments | Blockchain Payments |
| Stored Credentials | Centralized database stores millions of cards | No credentials stored anywhere |
| Database Breach | Single breach = millions exposed (Home Depot: 56M) | No database exists to breach |
| Third-Party Risk | Vendor access creates pivot point (Fazio Mechanical) | Vendors can’t access customer payment data |
| Phishing Effectiveness | Stolen credentials grant database access | Private keys never transmitted, phishing ineffective |
| Identity Theft | PII + payment data stored together | Pseudonymous addresses separate from identity |
| Data Tampering | Database records can be altered | Blockchain immutability prevents tampering |
| Single Point of Failure | One database compromised = catastrophic loss | Decentralized network, no central target |
| Recovery After Breach | All stored records exposed | Individual wallet compromise doesn’t cascade |
What Blockchain Doesn’t Solve (The Honest Limitations)
Blockchain payments eliminate centralized database vulnerability, but they don’t eliminate all security concerns:
Individual Wallet Security:
- If customer loses their private key or device gets compromised, their specific wallet is at risk
- But: This doesn’t expose other customers (unlike database breach exposing millions)
- Mitigation: Hardware wallets, multi-signature authorization, institutional custody for enterprise use
Smart Contract Vulnerabilities:
- Poorly designed smart contracts can have exploitable bugs
- But: Battle-tested protocols + code audits minimize risk
- Torsion approach: Uses only audited, established smart contracts from major issuers (Circle/USDC, Tether/USDT)
51% Attack (Theoretical):
- Attacker controlling majority of network could alter transactions
- Reality: Cost for Bitcoin/Ethereum is prohibitive ($20B+)
- Major payment networks are economically infeasible to attack at scale
The critical distinction: These are edge cases affecting individual wallets or theoretical attacks requiring billions in capital. Traditional payment breaches affect millions of customers at once through architectural centralization.
The $5.44 Million Question: What Does This Actually Cost?
Security leaders need ROI justification. Here’s the financial comparison.
Traditional Payment System: 5-Year Total Cost of Ownership
PCI DSS Compliance Costs (Level 1 Merchant Example):
- Initial implementation: $550,000 – $1,000,000
- Annual maintenance: $250,000
- Quarterly vulnerability scans: $24,000 annually
- Annual QSA audit: $75,000
- 5-year subtotal: $1M + ($250K × 5) + ($99K × 5) = $2.75 million
Average Breach Cost (If Occurs):
- Global average: $4.44 million
- U.S. average: $10.22 million (all-time high)
- Large-scale retail breach: $179 million (Home Depot)
Fraud and Chargeback Losses:
- E-commerce fraud: $48 billion annually across industry
- Every $100 fraudulent order = $207 total loss
- For $100M revenue e-commerce: ~$500K annual fraud losses
5-Year Total Exposure (Conservative Estimate):
- PCI compliance: $2.75M
- One average breach: $4.44M
- Fraud losses: $2.5M
- Total: $9.69 million
Blockchain Payment System: 5-Year Total Cost of Ownership
Transaction Costs:
- Payment processing: 0.5-1.0% (vs. credit cards 2-3%)
- Network fees: $1-5 per transaction (varies by blockchain)
- 50%+ cost reduction vs. traditional payment processing
Implementation with Torsion:
- Timeline: 2-4 weeks for most integrations
- Integration: REST API connects to existing e-commerce platform
- No infrastructure build: Torsion handles blockchain operations, merchant doesn’t operate nodes
Eliminated Costs:
- PCI DSS scope reduction as blockchain volume grows
- Breach insurance premiums (lower risk profile)
- Database breach exposure ($4.44M+ risk eliminated)
- Chargeback fraud (blockchain payments final once confirmed)
5-Year Savings Potential:
- Avoided breach cost: $4.44M
- Reduced PCI compliance (50% scope reduction): $1.38M
- Lower transaction fees (50% reduction on $100M volume): $5M+
- Total savings potential: $10.82 million+
Net 5-year advantage: $10.82M savings – implementation costs = $10M+ potential gain
The ROI Story for the Board
This isn’t a security expense, it’s a cost reduction initiative that also eliminates breach risk:
Year 1:
- Implement blockchain payments alongside traditional (hybrid model)
- Capture crypto-native customers, test infrastructure
- Transaction cost savings begin immediately (50%+ reduction)
Years 2-3:
- Incentivize blockchain adoption (pass along cost savings via discount)
- Shift 20-30% of transaction volume to blockchain
- PCI scope reduces proportionally (smaller cardholder data environment)
Years 4-5:
- Blockchain becomes primary payment rail, cards secondary
- PCI compliance costs drop 50%+ (reduced scope)
- No centralized database breach exposure
Real-World E-commerce Implementation: From Theory to Practice
CISOs and e-commerce leaders need practical implementation paths, not architectural theory.
How Blockchain Checkout Works for Customers
Current Customer Experience (Traditional Checkout)
- Customer clicks “Checkout”
- Enters card number, CVV, expiration date, billing address
- Credentials transmitted to merchant server
- Merchant stores data in PCI-scope database
- Transaction processes, credentials remain as breach target
Blockchain Checkout Experience (With Torsion)
- Customer clicks “Checkout”
- Selects “Pay with Stablecoin” (USDC/USDT displayed as $USD equivalent)
- Wallet interface opens (MetaMask, Coinbase Wallet, or built-in browser wallet)
- Customer sees: “Authorize $127.50 payment to MerchantStore”
- Clicks “Confirm” (wallet signs with private key, never shared)
- Transaction broadcasts, confirms in 30-90 seconds
- Merchant receives payment, never saw customer credentials
UX Considerations
- Advantage: No form fields, no typing card numbers (faster checkout for wallet users)
- Challenge: Requires customer to have wallet and stablecoins (adoption barrier)
- Hybrid solution: Offer both traditional cards and blockchain (customer choice)
Torsion’s E-commerce Platform Integration
Technical Architecture:
- REST API integrates with existing payment gateway
- Webhooks send real-time transaction status updates
- Supported platforms: Shopify, WooCommerce, Magento, BigCommerce, custom builds
- ERP integration: NetSuite, SAP, QuickBooks, Xero for accounting reconciliation
What Merchant Infrastructure Looks Like:
- Payment gateway layer: Torsion API sits alongside Stripe, Adyen, or existing processor
- Blockchain node access: Handled by Torsion (merchant doesn’t operate infrastructure)
- Settlement: Auto-conversion from stablecoin to USD if desired (merchant receives USD)
- Accounting: Stablecoin payments treated as cash equivalents, full audit trail provided
Implementation Timeline:
- Week 1: Technical integration (REST API, webhook configuration)
- Week 2: Testing with test transactions on blockchain testnets
- Week 3: Production deployment with monitoring
- Week 4: Customer rollout, support documentation
- Total: 2-4 weeks from kickoff to live blockchain payments
The Three-Phase Migration Strategy
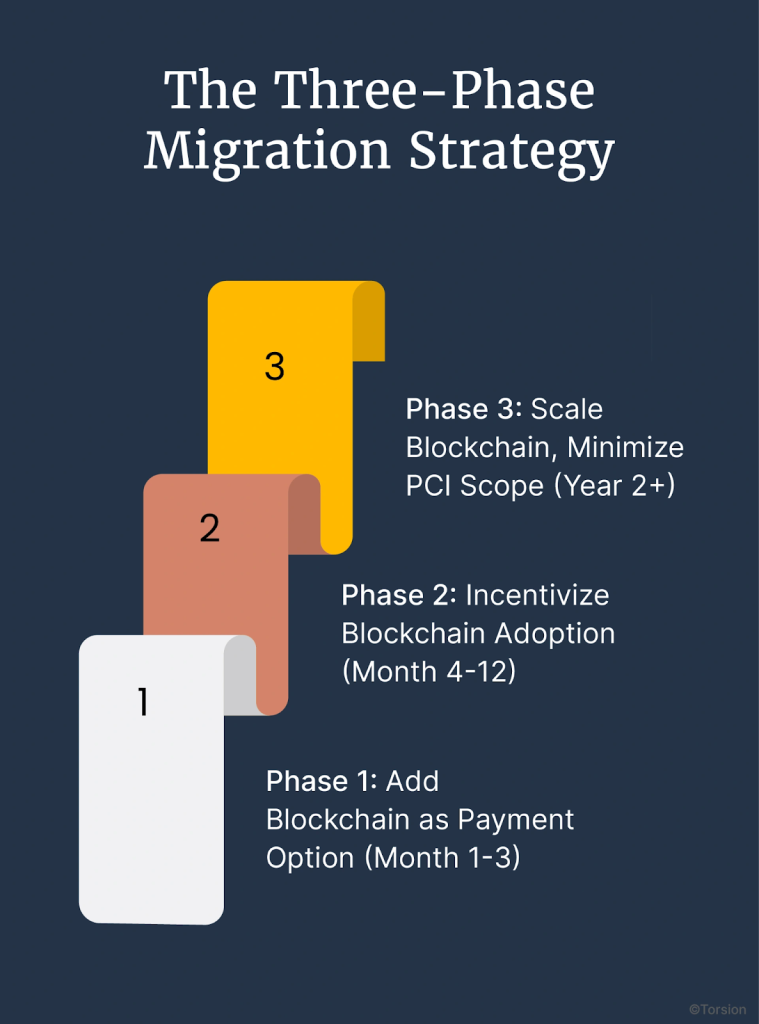
Phase 1: Add Blockchain as Payment Option (Month 1-3)
Implementation:
- Integrate Torsion’s blockchain payment API alongside existing card processor
- Display “Pay with Stablecoin” option at checkout (in addition to credit/debit)
- Start with crypto-native customers, early adopters
Benefits:
- Test infrastructure with low-risk cohort
- Capture customers who prefer stablecoin payments
- Begin transaction cost savings on blockchain volume
- No disruption to existing customer base
Phase 2: Incentivize Blockchain Adoption (Month 4-12)
Implementation:
- Offer 2-5% discount for stablecoin payments (pass along merchant cost savings)
- Marketing campaign: “Pay with USDC, save 5%”
- Target segments: international customers, crypto-aware demographics
Benefits:
- Shift 20-30% of transaction volume to blockchain
- Reduce PCI DSS scope as cardholder data environment shrinks
- Lower transaction fees (0.5-1% vs. 2-3% cards) enable discounting
- Begin PCI compliance cost reduction
Phase 3: Scale Blockchain, Minimize PCI Scope (Year 2+)
Implementation:
- Blockchain becomes primary payment rail, cards secondary option
- Cardholder data environment reduced to minimal scope
- PCI compliance costs drop 50%+ (fewer systems, smaller environment)
Benefits:
- $100K-$250K annual PCI compliance savings (Level 1/2 merchants)
- Centralized payment database risk minimized
- Transaction cost savings compound annually
- Architectural breach vulnerability largely eliminated
Use Cases Where Blockchain Eliminates Specific Risks
High-Fraud Verticals:
- Industries with >1% fraud rates: nutraceuticals, supplements, CBD, adult content
- Blockchain benefit: Zero chargeback fraud (payment final once confirmed)
- Database benefit: Can’t breach credentials that were never stored
International E-commerce:
- Accept payments from markets blocked by traditional processors
- Eliminate payment processor geographic restrictions
- Security benefit: Customer credentials never cross borders or jurisdictions
Subscription/SaaS Businesses:
- Recurring payments without storing card data
- Reduce involuntary churn from failed payments (no card expirations)
- Breach elimination: No database of active subscriber cards to steal
B2B Marketplaces:
- High-value transactions ($10K-$1M+)
- Buyer and seller need payment finality (no chargeback risk)
- Security: Eliminates stored credential exposure for large transactions
What Torsion Handles (So You Don’t Need Blockchain Expertise)

The Infrastructure Gap:
- E-commerce platforms lack native blockchain payment integration
- Building in-house: 12-18 months, $5M+ development cost
- Hiring blockchain engineers: $150K-$300K salaries, hard to find talent
Torsion’s Bridge from Traditional to Blockchain:
Technical Integration:
- REST API connects to Shopify, WooCommerce, Magento, BigCommerce
- Webhooks for real-time transaction updates
- Auto-conversion: Customer pays USDC, merchant receives USD
- Merchant’s development team treats it like any payment API
Compliance & Security:
- GENIUS Act (U.S.) and MiCA (EU) compliance built-in
- AML/KYC through Chainalysis and TRM Labs
- SOC 2 Type II certified infrastructure
- Transaction monitoring and suspicious activity reporting automated
Blockchain Operations:
- Node infrastructure managed by Torsion (merchant doesn’t operate nodes)
- Network fee optimization (routes through lowest-cost chains)
- Wallet integration partnerships (MetaMask, Coinbase Wallet, WalletConnect)
- Merchant’s team never touches blockchain directly
Accounting & Reporting:
- Stablecoin payments treated as cash equivalents (standard accounting)
- Auto-reconciliation with ERP systems (NetSuite, SAP, QuickBooks, Xero)
- Full audit trail with blockchain transaction IDs
- Monthly compliance reports for CFO/CISO
The Value Proposition:
Torsion bridges the gap between traditional e-commerce infrastructure and blockchain payment rails. Security teams get architectural breach elimination without learning Solidity. Operations teams get 50% lower transaction costs without disrupting checkout flows. Just as Torsion bridges AI strategy to execution, we apply the same methodology to payment infrastructure: you understand the security benefits, we handle the technical implementation.
The Honest Reality: What Blockchain Doesn’t Replace (Yet)
Security leaders distrust vendor pitches that promise to solve everything. Here’s the balanced perspective.
Limitations and Trade-Offs
Customer Adoption Curve:
- Most consumers still use traditional payment methods (cards, PayPal, Apple Pay)
- Blockchain payments represent growing but minority segment currently
- Reality: E-commerce needs hybrid model (both traditional and blockchain)
User Experience Friction:
- Customers need digital wallets (MetaMask, Coinbase Wallet, etc.)
- Blockchain terminology can intimidate non-technical users
- Wallet setup adds friction compared to saved card autofill
- Mitigation: Simplified wallet onboarding, one-click checkout partnerships improving
Volatility Concern (Addressed by Stablecoins):
- Bitcoin/Ethereum price fluctuation creates accounting complexity
- Solution: Torsion uses only stablecoins (USDC/USDT) maintaining $1 peg
- Stablecoins backed 1:1 by dollar reserves, audited monthly
- No volatility exposure for merchant or customer
PCI Compliance Still Required (For Card Payments):
- Until blockchain reaches majority adoption, cards remain necessary
- Merchants maintain PCI infrastructure for traditional payment option
- Benefit: Incrementally reduce scope as blockchain volume grows
The Hybrid Model Reality
Near-term (2025-2027):
- Most e-commerce runs dual payment systems
- Traditional cards for mainstream customers (80-90% of volume)
- Blockchain for early adopters, international, crypto-native segments (10-20%)
- PCI scope reduced but not eliminated
Medium-term (2028-2030):
- Blockchain adoption accelerates as wallet UX improves
- Merchants incentivize shift through discounts (pass along cost savings)
- Traditional cards become secondary option (30-40% of volume)
- Significant PCI compliance cost reduction
Long-term (2030+):
- Blockchain becomes primary payment rail for e-commerce
- Cards maintained for edge cases, older demographics
- Database breach vulnerability largely eliminated
Regulatory Framework Now Established
Historical concern: “Is this even legal? What if regulators shut it down?”
Current reality (October 2025):
- GENIUS Act (U.S., July 2025): Federal framework for stablecoin regulation
- MiCA (EU, December 2024): Comprehensive crypto asset regulation including stablecoins
- Stablecoins now have clear compliance path, not regulatory gray area
- Torsion infrastructure compliant with both frameworks from day one
Next Steps for Security Leaders
If your organization processes significant e-commerce volume:
Evaluate the architectural alternative: Blockchain payments don’t make databases more secure, they eliminate the database.
Assess hybrid implementation: Add blockchain alongside cards, shift volume incrementally, reduce PCI scope over time.
Calculate 5-year TCO: PCI compliance + breach risk + fraud losses vs. blockchain implementation + lower transaction costs.
Engage Torsion for technical assessment: REST API integration with your e-commerce platform (Shopify, WooCommerce, Magento, custom), 2-4 week timeline.
The Architecture That Eliminates the Breach
Home Depot’s $179 million lesson was clear: centralized databases storing millions of payment credentials create catastrophic breach exposure. Target’s 70 million compromised customers confirmed the pattern. Yet e-commerce continues building the same architecture.
Blockchain payment rails don’t improve that architecture. They replace it.
No stored credentials. No centralized database. No honeypot.
The regulatory framework exists (GENIUS Act, MiCA). The technology is proven (stablecoins processed $14 trillion in 2024). The implementation path is clear (2-4 weeks with proper infrastructure partners).
The question is: How much will your breach cost before you eliminate the vulnerability?